Hello to all relatives (and the means YOU),
I want to get my thoughts out there about operating systems. If a new computer is on your list for holiday giving or receiving, you'll want to be forewarned about what is on the shelf at your local computer store.
The operating system is what makes your computer work from the moment you turn it on until you turn it off.
When you turn on a computer, the very first screen displayed will be the manufacturer: Dell, or HP or Lenovo.
The second thing you will see displayed will be the operating system. It will display, “Windows 7” or “Windows XP” or “Windows Vista.” These are the most popular. A few manufacturers are using Linux, so you might see “Ubuntu” or “Debian” or “Red Hat.” Only three are listed, but there are many more Linux operating systems.
There are also Apple computers to choose from. Apple is a very closed minded company that allows only a limited, select list of software to run on their computers. Their computers are expensive.
The use of Apple computers is for a select bunch of people and I will not get into their product line or software at all.
I want to warn everyone about a bad product that Microsoft sold for a couple of years.
It is called “Windows Vista.”
If you have this software operating your computer, get rid of it and replace it with Windows 7.
If you have already bought a computer as a holiday gift that has Windows Vista installed on it, take it back, NOW and insist on getting Windows 7 for your new computer.
Sometimes a store will drop the price on a computer with Windows Vista just to get it off of the shelf. Unless you are really good on a computer, insist on Windows 7.
Upgrading your computer: If you need help upgrading from Windows Vista to Windows 7, I will be happy to help. I can even help you find the best price (about $100 these days).
New computer: For those of you who are buying a new computer, make sure that it does not have Windows Vista. Please, please do not buy a computer that has Windows Vista.
If you step up to a computer at the store, make sure it does not have Windows Vista. You can ask a salesperson, or do the following:
Touch the Windows logo key (look to the left) and touch the Pause/Break key.
The System Properties box will pop up and will look something like this: (be sure you are on the General tab. This one shows that the System: is Microsoft Windows XP.
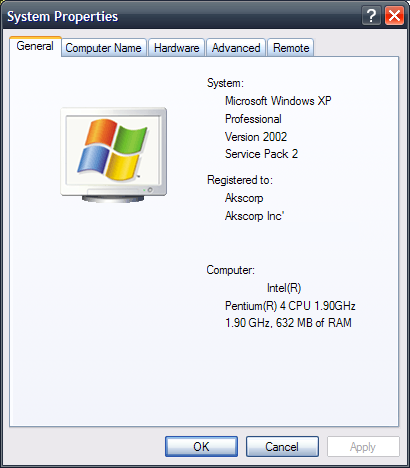
Everyone is entitled to their own opinion and this is my opinion: Microsoft Vista operating system is a bad product.
Thank you for reading. If you need help or want to state your point of view, please don't be shy about asking; it could save you a lot of money and frustration.
I would like to take a few minutes to tell you a bout an operating system that is FREE!!
That is Linux. It comes in many different flavors or Distributions (sometimes called Distros).
These days a lot of companies are designing their own distribution with cute names like Ubuntu or Knoppix.
Linux software engineers and pro-Linux organizations want Windows users to be able to move over to Linux without any problems. Also, there is more and more software available that supports Windows, Linux and other types of operating systems. The big thing about Linux, and software that is used with it, is that is is free.
The computers that are currently being manufactured are made to standards that make it easier for any operating system to work on any computer.
When you buy a computer, you expect it to work. The Microsoft company has their stickers on computers indicating that that computer was designed to specifically run on the Microsoft operating system. So what is happening now is that the creators of the different Linux distributions are trying very hard to make it so that a person can install their, Linux, operating system without any problems.
It is working, their efforts to get a Linux operating system installed and working without a hitch are getting closer and closer to that point, making the change-over from Windows to Linux transparent.
Opinion: At this point in time, if I were to buy a brand new computer, I would spend the extra money to buy one with the Microsoft Windows operating system, specifically Windows 7. If you can afford Windows Office, I would recommend that as well.
Linux designers are making great strides toward that transparency that I mentioned in the previous paragraph but they aren't there yet.
Blessing, love and joy to you all this holiday season,
Holiness David
Blessing, love and joy to you all this holiday season,
Holiness David
Welcome to the home of love, where your computer gets to know of hugs. Take the time to give it love, to ensure the spine stands, on the test of time (until you update protection files again). For only you can operate the golden rule, do unto your computer, who knows who to fool. But we do outwit the slyest fox, when we give love instead of gloves (put them up, combative forces). The greatest part of protection is clear, the smooth operation of moving in space is dear (world wide web). Protect my computer God above to bring the Angels down below. Bless and bless the common place, to be rest assured that all is grace.



 22 days ago by
22 days ago by 


 Obviously, the first thing you need to do is download Spybot-Search and Destroy from our
Obviously, the first thing you need to do is download Spybot-Search and Destroy from our  The file you have downloaded will be named spybotsd162.exe or similar. To install Spybot-Search and Destroy, all you have to do is run the file, and the installation program will start (if you have downloaded with Internet Explorer, the download dialog will give you the option to open the file directly). The installer will show you the license and ask you for the installation location. You can go with the default settings here and just click your way through the installer by using the Next button.
The file you have downloaded will be named spybotsd162.exe or similar. To install Spybot-Search and Destroy, all you have to do is run the file, and the installation program will start (if you have downloaded with Internet Explorer, the download dialog will give you the option to open the file directly). The installer will show you the license and ask you for the installation location. You can go with the default settings here and just click your way through the installer by using the Next button. The first time you start Spybot-Search and Destroy, it will display a Wizard, a small window helping you through the first steps. It gives you the possibility to add or remove the icons you have or haven't created during install, for example. Let's just say you want them and proceed to the next page.
The first time you start Spybot-Search and Destroy, it will display a Wizard, a small window helping you through the first steps. It gives you the possibility to add or remove the icons you have or haven't created during install, for example. Let's just say you want them and proceed to the next page. After the tutorial has finished, you may find yourself on the Settings or Update page. As the default settings are ok right now, and you've already updated, let's ignore them for now and do the first scan.
After the tutorial has finished, you may find yourself on the Settings or Update page. As the default settings are ok right now, and you've already updated, let's ignore them for now and do the first scan. At this point, you could just jump to point 7, and remove the results. Instead we recommend that you first have a look at what all the stuff is that Spybot-Search and Destroy detected. The first thing you should know is to distinguish between the
At this point, you could just jump to point 7, and remove the results. Instead we recommend that you first have a look at what all the stuff is that Spybot-Search and Destroy detected. The first thing you should know is to distinguish between the  The Immunize function prevents e.g. Tracking Cookies from entering your system. Immunize works with Mozilla Firefox, Internet Explorer and Opera, allowing you to adjust specific settings of the browser to block known spyware installers, (and similar baddies) already included in Spybot-S&D's database. You start the Immunize function by clicking on Spybot-Search and Destroy → Immunize on the left navigation bar.
The Immunize function prevents e.g. Tracking Cookies from entering your system. Immunize works with Mozilla Firefox, Internet Explorer and Opera, allowing you to adjust specific settings of the browser to block known spyware installers, (and similar baddies) already included in Spybot-S&D's database. You start the Immunize function by clicking on Spybot-Search and Destroy → Immunize on the left navigation bar. Resident TeaTimer prevents unwanted files from being installed – no matter how – on your system. It monitors the processes called/initiated perpetually. If known malicious processes want to start, TeaTimer immediately terminates them, giving you three options how to deal with this process in the future:
Resident TeaTimer prevents unwanted files from being installed – no matter how – on your system. It monitors the processes called/initiated perpetually. If known malicious processes want to start, TeaTimer immediately terminates them, giving you three options how to deal with this process in the future:  Since Spybot-Search and Destroy 1.6 the TeaTimer uses our database where known files are rated as good or dangerous. This database contains several hundreds of thousands entries and is enlarged continuously. Nonetheless now and then there are files which are not contained yet. In these cases and if you use older Spybot versions Resident TeaTimer will ask your permission for every change. If you are not sure if you should allow the change, there is a simple rule of thumb:
Since Spybot-Search and Destroy 1.6 the TeaTimer uses our database where known files are rated as good or dangerous. This database contains several hundreds of thousands entries and is enlarged continuously. Nonetheless now and then there are files which are not contained yet. In these cases and if you use older Spybot versions Resident TeaTimer will ask your permission for every change. If you are not sure if you should allow the change, there is a simple rule of thumb: Of course it is possible to revise each of your personal decisions. That could be necessary if you have denied some process which turns out as a good one later. You do so by right clicking on the TeaTimer symbol in the system tray - it is the blue one with the lock. (If you cannot see the symbol, it is probably hidden. Just click on the arrows in the system tray to show all hidden symbols.) A window appears where you have to click on Settings to modify your personal lists of registry changes and processes.
Of course it is possible to revise each of your personal decisions. That could be necessary if you have denied some process which turns out as a good one later. You do so by right clicking on the TeaTimer symbol in the system tray - it is the blue one with the lock. (If you cannot see the symbol, it is probably hidden. Just click on the arrows in the system tray to show all hidden symbols.) A window appears where you have to click on Settings to modify your personal lists of registry changes and processes.










BlossomingDeerPetals(Red)BlueLakePeopleLeadingMigration.jpg)














